Being the latest version of Windows to come from Microsoft, Vista has many new features which has made it one of the most popular operating systems on the Internet. However, it still relies on a part of your system called the 'registry', which is often referred to as the "Achilles Heel" of Windows - the registry. To fix this, you just need to use a registry cleaner, but with Vista being so new... which one is the best?
Registry cleaners have all been designed to do the same job, except some of them do that job much better than others. They have all been developed to clean out a part of your computer called the 'registry', which is the central database for your PC. This database stores all your settings and options for your computer, allowing Windows to save everything from your desktop background to your latest emails, even if it's turned off and on again.
The registry is one of the most well-used parts of your system and unfortunately, it's also where most of the problems for your computer are born. Because Windows is constantly using 100's of different registry files, it's always getting confused about which ones it has open. This makes it confused, making it save them all in the wrong way, making the files corrupt and damaged. This makes them incredibly hard to read, slowing your computer down and causing errors.
To fix this problem, registry cleaners have been developed to clean out all the corrupted files from the registry database. However, because Vista is so new, many of the old registry cleaners simply don't work on it. The best Vista registry cleaner is one which actually scans through your registry, finds the most problems and fixes them all for you. And as Vista has introduced many new features to Windows, it's important that you have a cleaner which recognizes which files it should clean and which it should leave.
That's why you need a cleaner which is up to date and ready to handle all the latest problems that Vista will throw at it. These type of cleaners are normally created by professional developers, who have the time and resources to continually update their software. Cleaners such as RegAce are in this category, and are extremely effective because they know the latest Vista problems, so they can fix them all instantly.
From our experience, the best Vista registry cleaner is one called RegAce
Uninstal.exe is a Windows uninstall program. But in some specific set of conditions, the process might replace FAT32 MBR, thereby resulting into inaccessible primary partition (usually C:) of system. Such situations require performing steps like recreating the primary partition and reinstalling Windows. So, to restore the lost information, you should use your recent data backup available or scan your affected hard drive by using powerful data recovery applications.
Consider an instance, you try to run Uninstal.exe in real mode, but instead of expected behavior, you encounter an error message describing that Winundo.dat is missing or damaged. The error further gives you an option to continue. Clicking either of the options (Yes or No) gives you the below error message:
"Invalid system disk"
This error appears after the system restarts.
Cause
The above behavior is exhibited when the following set of conditions is true:
You have converted your primary drive to FAT32 file system using Drive Converter utility
You have run Uninstal.exe from Windows startup disk or restored it manually
You have run Uninstal.exe in real mode
Or
You have installed Windows
You have used a third-party disk partitioning utility
You have run Uninstal.exe
In the former case, running Uninstal.exe replaces FAT32 MBR with backup of FAT16 MBR and you observe the above error messages. However, in the latter scenario, the issue is observed if partitioning utility affects the partitioning structure of the disk.
Solution
To resolve such issues, you need to perform these steps in order:
Recreate you primary drive using utilities like Fdisk.exe
Reformat the primary drive
Reinstall Windows and other applications
Restore data from backup
At times, you cannot restore from the present data backup. It might occur if backup is damaged or not updated completely. Thus, to cope up with such situations, you should use data recovery software. These are advanced data recovery tools built with indigenous technology to safely recover the lost information from logically crashed drives. Such tools provide you interactive user interface, powerful recovery features and several other added characteristics.
Stellar Phoenix Windows Data Recovery is a premier application to recover and restore lost data that supports Windows 7 (currently in RC 1), Vista, XP, 2003, and 2000. This read-only data recovery Software provides powerful features like Disk Cloning, Disk Imaging, Drive Status, RAW File recovery etc. It is compatible with FAT32, VFAT, NTFS and NTFS5 file systems.
File Systems
EXT 2 is the historical system of the Linux platform and was marketed in 1993. It has since been replaced by E 3, which has added some new features including the most notable being the logging. EXT3 is the default file system for most Linux distributions.
Like many other UNIX file systems, the main structure is very similar to the original UNIX Fast File System (FFS). The score is divided into groups of cylinders, and each of these groups contains initially Superblock, Group Table, the data bitmap, a bitmap node, node files and data. However, more recent versions of E 2 and Group 3 have hollow cylinder that contains only nodes and data files.
The EXT file systems 2 and 3 have a fixed number of nodes file and they are drawn on the score by the superblocks and Group Tables. These nodes files are data structures containing information about nt files stored in some file systems:
* The file type
* Access rights
* Owners
* The timestamps
* The size
* The data block pointers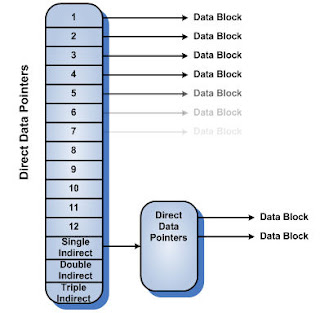
The pointer data block are the node which sends the data file on disk.
The first twelve are pointing to the physical blocks of data. The first 12 fields (out of 15) contain the addresses of the first 10 blocks of file data (with an address block). If the blocks on which point the first 10 fields are sufficient to contain the file, the fields 11, 12 and 13 are not used. H owever, the three point to indirect blocks of data (single, double and triple indirect ion s). L a simple indirect ion contains the address of a block of direct pointers (called block address) as shown in the diagram. Thus, the address block contains pointers to data blocks (256 pointers). The double indirect ion points to a single block containing single indirect pointers. However, this block of addresses is pointing to 256 blocks of data it points to other blocks of 256 addresses. These are the 256 blocks of addresses that point to 256 blocks of data. L ogiquement triple indirect ion points to a block of double indirect pointers (to follow the same reasoning as above). This can be very difficult to visualize, but basically every step of indirection allows the amount of data to be sent to the exponential.
XFS
XFS was originally developed by SGI in 1993. The project was to overcome some limitations in terms of performance and extension of the FFS. This is a file system journaling 64-bit high performance. It was first published in 1994 with IRIX V5.3 and 2000, SGI released the source code open. It was then formally included in the Linux kernel since 2003. The structure of XFS is very similar to that of FFS at first sight. It keeps the system of cylinders Groups splitting the partition, but the groups named for the award and he also uses superblocks and filesystem nodes to contain the metadata files, but the similarities in content and stop functioning at that level .
Unlike FFS, the file system does not have a fixed number of knots of pre-allocated files on disk. In its place, each group should monitor the allocation space and dynamically allocate nodes file according to the needs expressed by the file system. These nodes files are organized in a balanced tree B +, which makes traversing the directory structure much faster than the traditional list system implemented in FFS. However, to maintain high performance, the B + tree is kept balanced thanks to a grant of intelligent nodes and files it requires relatively advanced algorithm. The nodes also use XFS file extension (run lists) to send data instead of treating the individual blocks of data as FFS, and it adjusts to the best size for your important files.
XFS journaling also provide an opportunity for recovery of file system in case of crashes and power outages. However XFS reviewed only the file system metadata while the volume can be repaired and loaded on it and can still be a cause of data loss.
Another feature of XFS has delayed allocation. First, the data are stored in memory. Then these data is actually written to the file system where the cache is cleared by the operating system. This method of allocation wave allows for a certain delay in the action to obtain the necessary data to allocate the most intelligent way possible. The main advantages of this approach is the dramatic decrease of fragmentation, especially with files that grow slowly and often reduces the CPU overhead.
JFS (Journaled File System)
In 1990, IBM produced a first draft JFS with AIX version 3.1. Later in 1999, IBM brought it under OS / 2 and published a version of JFS in the open source community and in 2006 was the stable version of Linux.
The philosophy behind the design JFS is comparable to that of XFS. They aim to overcome many limitations of FFS performance in a very similar way, although recent implementations are different. Both file systems use metadata logged to provide the file system is a possibility of recovery, nodes dynamically allocated files and extensions to address the area of data and also the diagram of the transverse B + tree. For more information, see the section XFS.
LVM
Managing logical volumes (in English, logical volume management or LVM) is a method to overcome some limitations of using traditional methods partition to allocate storage space on the media. Generally the features included are:
* File System Spanning and software RAID (Level 0, 1 and 5)
* Resize volume groups and logical volumes
* Photo (the hard disk and partition are concerned) or snapshots
Traditionally space on hard disks is divided into partitions on which file systems are written directly. LVM works a little differently, the disks are always allocated using them, but they are considered "physical volumes" on LVM. Hard drives, hard disk partitions, RAID volumes or logical units from a SAN form the physical volumes. Then we concatenate these physical volumes in "volume groups". The volume group can then be allocated to a form of logical volumes on which file systems reside. The diagram below shows a relatively simple example of how LVM could be used.
Nowadays, cases of UNIX versions of adopting their own variations of LVM are very common. According to the seller they have names and different functions. Linux also has an LVM which is based on the Hewlett Packard UNIX version. One feature missing on both the HP and the Linux LVM is that they have no implementation to manage fault tolerance by gender, so no software RAID 5.
Windows 2000, 2003, XP and Vista have an equivalent system called Logical Disk Manager, which offers similar capabilities.

Kroll Ontrack's engineers have the expertise and experience to recover data from your UNIX and Linux systems, either a single terminal server or a RAID 5.
Whatever the situation of data loss, Kroll Ontrack is using the tools and techniques of the industry to ensure a quality service unmatched. Here is a small sample of the types of problems that we get regularly:
* Kernel panic and machines that can start more
* Formatted or deleted partitions
* Files and folders deleted or missing
* File systems that are corrupt or not loaded (to mount)
* Crash of the system and fsck failure
* RAID configuration lost / damaged
About UNIX - Linux
* UNIX
UNIX is an operating system multi-user, multi-tasks originally developed in 60 years by the laboratories AT & T Bell. Most UNIX is written in the C programming language and is therefore capable of operating over a wide range of architectures. Equipment suppliers, such as SCO, SGI, IBM, Hewlett Packard and Sun offer their own version of Unix to run on their high-end server.
* Linux
Linux, sometimes called GNU / Linux is an operating system POSIX. The GNU project began in 1984 with the aim of creating a free version of UNIX. The project lacks a core operating fully until 1991 when a 3rd party kernel called Linux was launched by Linus Torvalds. The Linux kernel is normally published in conjunction with various packages from the GNU project and other sources. Thus, the main success of Linux is its modular design, the user can adapt its own systems to the Linux kernel.
Data Recovery UNIX / Linux
We are able to speak on a wide range of UNIX file systems and Linux in the industry. Although our current tools do not support your transfer, we have a team of software developers capable of developing Just In Time (JIT) to modify or create new tools to meet your expectations.
will continue...
Eminem on Family Guy and Stewie vs 50 cent & Eminem
Posted by ALMeD Labels: 50 cent, comedy, eminem, family guy, stewieEminem will appear on the hit cartoon series Family Guy this Sunday. The rapper will be featured in several programming breaks through the entire night on FOX. What will Eminem be doing on Family Guy? Well, as Em’s manager Paul Rosenberg says, “What? Why? Tune in and find out what Stewie and Em chop it up about… this is already classic TV material.”
And........ Stewie vs 50 Cent & Eminem :)

Backing up data is an important issue. Users do not want to lose data. Data loss is difficult to compensate. Therefore, reproduction of data is important. I accidentally deleted files, errors ... There are many data backup tool. A data backup program on your computer, CD or DVD, external hard disk drive or USB flash drive as possible. But this path can be expensive. This is done through online data backup. Online data backup or data will be saved only for this file is stored via the internet means.
Online data backup easy means that your folders or data are saved or stored through the use of an internet. One may store and restore folders on an online account by just easy downloading the program given by a absolute website. Once the said program is installed in your computer, your folders are already secured. For all that, in this type of online data backup, one must all the time have an internet connection when using the computer.
CLİCK for backup...
Recover deleted files on Linux (Ubuntu)
Posted by ALMeD Labels: Data Recovery, images, jpeg, ubuntu recovery
sometimes if you happen to be a little head in the air and delete files on your Windows PC, there is a plethora of apps to recovery files (even those deleted from the Recycle Bin).
Aaaaah, fear no more because it is also possible to simply retrieve the files through a command line tool called Foremost, which was originally developed for the special investigation service of the U.S. Air Force ...
Recovering a deleted file from a simple concept ... when you delete a file, only the pointer to it is broken but it is not immediately re-écrabouillé with other data. The file is still physically present on the hard disk. Obviously, the longer you wait before you recover a file, it most likely to disappear forever.
I will speak with Ubuntu is because I use distrib. I do not know how it goes for other distrib but in principle, it remains the same. To install Foremost, you must activate the Universe repository and enter the following command line (or via Synaptic):
sudo apt-get install foremost
Then you must know the partition where you want to recovery files. (eg /dev/sda1)sudo foremost -w -i /dev/sda1 -o /recovery/foremost
For example, to retrieve deleted jpg images, you must type:sudo foremost -t jpeg -i /dev/sda1
Foremost will then create a directory named "output" in which he put all the files recovered. Obviously, if the images have begun to be crushed, you'll get half of the images but it is already ...There are obviously lots of other options but the recovery ennoncer here would be too long (and I do not master all) but I recommend you read the man page Foremost here.
Source
Other Post:
Importance of Disk İmages and Data Recovery
3 Freeware Data Recovery Tools - Easy Way
How to Speed Up Windows XP in Seconds ? Easy Way
Hard Disk: Maintenance and Data Recovery - 2
Posted by ALMeD Labels: Data Recovery, Maintenance CD, Recover Damaged CD The test protocol
The test protocol
Height of bad luck for us but perfect condition to illustrate this article, we have been able to "enjoy" a serious failure relegating one of our PC to the state of wreckage or almost. Indeed, for completely unknown reasons it has definitely ceased to function by taking the same time all the data stored on both disks MAXTOR S-ATA I Diamond Plus 9 with a capacity of 80 GB each and only 14 old months. Our disappointment subsided, we used one of these two discs (the second drive had a mechanical failure too serious to the point of not being detected properly by the bios on the motherboard) to test the software to recover data as GetDataBack, Undelete 5.0 R-studio ...
We went even further by adding in our protocol, the human factor, ie by carrying out various operations on other discs test: formatting, repartitioning, suppression of voluntary programs and / or files, fragmentation of files and finally deleting RAID cluster, all with the sole aim to be as close as possible the actual conditions of use of most of us.
For this reason we have used hard drives Western Digital Raptor 74Go as MAXTOR Diamond Plus 10 250GB P-ATA on which we installed Windows XP Pro SP2 and a variety of programs (games, utilities, miscellaneous, office, multimedia, etc ...). For RAID 0, two disks of 160GB Barracuda 7200.07 S-ATA Seagate and mounted in the following machine:
* 2x512 MB DDR 400 2.2.2.5 of Corsair TwinX
* Motherboard MSI K8N Diamond SLI nForce 4
* Map 3D RADEON X800XT PCI Express Asus
* DVD-ROM and DVD-ROM NEC ND-2500A
* Hard Drive Seagate Barracuda 7200.07 S-ATA 200GB NCQ and for the operating system disk and P-ATA Barracuda 7200.07 200 GB in a housing mounted 5 ¼ inch external FireWire 400/USB 2.0 for storage of data recovered.
Other Post:
Importance of Disk İmages and Data Recovery
3 Freeware Data Recovery Tools - Easy Way
How to Speed Up Windows XP in Seconds ? Easy Way
Hard Disk: Maintenance and Data Recovery - 1
Posted by ALMeD Labels: Data Recovery, Maintenance CD, Recover Damaged CDObviously, it is possible to make a backup of your data by several methods: optical engraving (CD-RW/DVD-RW), backup to external media (hard disk, USB, tape, ZIP, etc ... ) or create a disk image ... very active on most recent motherboards, RAID 1 or RAID 0 +1 is a very good solution to control fault tolerance, provided, however, have two disks identical to a minimum.
Although the hardware failure is a major cause for loss of data, it is a more frequent human error. Whatever the cause, in both cases, you lose your data. But perhaps not entirely. Indeed there are solutions to recover data and although we do not offer "the" miracle solution 100% reliable, it is possible to minimize a risk of loss and also to maximize the chances of retrieving data. We shall therefore in this article give you practical advice on basic maintenance on your hard drive. We will also review two software to recover data. As you can see, our goal is not to be comprehensive and test every software available (they are many) but simply to clarify you on how to manage your disks and show you that it is always possible to recover data that was thought lost ...
1) If it is dust, take a soft cloth or cotton and gently rub the CD (or DVD), taking the CD with your finger in the central hole. Do not touch the surface engraved!
2) If the DVD is fatty or oily, mix baby shampoo in very hot water and use cotton (clothing or soft) to rub the surface of the CD recorded with this solution. Wait while the CD is dry before you read it or store it in its box.
5) Do not rub the CD by following the direction of rotation of the latter but still rub the hole center to the edges with several return.
Despite the intensive cleaning, your DVD player still refuses to play your CD! Do not panic, this is still not completely screwed!
There are software programs that can help you recover your valuable data:
1) CD Check - Detects and recovers damaged files on CDs. CD Checks can also be used to test the proper operation of your CDs and prevent any problems.
2) Unstoppable Copier - Available for Windows and Linux. It is a freeware that can copy files from CD with a few concerns such as bad sectors, scratches or that just causes errors when reading data. Normally with Windows, when your computer can not copy a damaged file, it will give up and remove the small piece of data they managed to copy. Unstoppable Copier will prevent this and continue copying until the end. Each data innaccessible will be replaced by a blank.
3) IsoBuster - Supports CD and DVD. It has tons of options for data recovery and the standard version is free!
Other Post
The Symptoms of File Damage
3 Free Online Backup Websites
Software, Solution for Crashed Hard Disk
 Knowledge of disk imaging is necessary for all people with several aspects of data recovery. A regular computer user should be aware that the data stored on hard disks are vulnerable and may be lost due to assorted reasons, most of which may not be in your control.
Knowledge of disk imaging is necessary for all people with several aspects of data recovery. A regular computer user should be aware that the data stored on hard disks are vulnerable and may be lost due to assorted reasons, most of which may not be in your control.
In this way, even if you lose your data, you can use the reader, as with using the disk image, data recovery a breeze. Image file, in fact, an exact copy of the partition table and file system. It is also a kind of phantom images, in which the Nitty Gritty of the operating system, system settings and drivers in the image.
Thus, after a data recovery with a ghost image, you can create a desktop and system configuration, it is exactly the same as your hard disk is blocked!
So, after you make a recovery data using a Ghost image, you can start a desktop and system configuration, it is exactly the same as your hard disk crashed!
AmeriVault Online Backup Website Providing online services, reliable and useful site. Online data backup, data replication, e-mail archiving. Automatic disk solutions. Your problem is corrected with a few clicks. Disk-to-disk solutions that deliver all automation, amazing security. Starting online backup...
Providing online services, reliable and useful site. Online data backup, data replication, e-mail archiving. Automatic disk solutions. Your problem is corrected with a few clicks. Disk-to-disk solutions that deliver all automation, amazing security. Starting online backup...
System Recovery Online Backup
 The best online backup site, my recommendations. Theft, viruses, accidental deletion from solution. Data recovery, repair, online data archiving, scheduled daily backup... Online storage also makes your data easily accessible and enables you to remotely retrieve files from a home or office computer, and share your files with co-workers.
The best online backup site, my recommendations. Theft, viruses, accidental deletion from solution. Data recovery, repair, online data archiving, scheduled daily backup... Online storage also makes your data easily accessible and enables you to remotely retrieve files from a home or office computer, and share your files with co-workers.Maximum privacy and professional online backup service. Go for CLİCK.
NovaStor Online Backup
 An effective online backup service. Three services. network backup, online backup and desktop backup.
An effective online backup service. Three services. network backup, online backup and desktop backup.CLİCK
The symptoms of a missing file are pretty obvious (you won’t be able to find it), but the symptoms of file corruption can run the gamut. Some of the symptoms of file corruption include
-
A file that won’t open when you click it; the operation either puts you at an hourglass or does absolutely nothing.
-
You see the file you want to open in a folder list but when you try to open it, you’re told the system cannot find the file or it’s not a valid file.
-
A file opens with a wide range of error messages, not all of which indicate corruption.
-
A file opens to display what appears to be garbage characters as if you opened the file using the wrong program

-
As the file is opening, a low memory warning appears, or you’re told you cannot open the file because you have too little available memory.
-
Windows prompts you to tell it what program to load this file with, when the file is of a type already associated with and recognized by that program (such as .doc files in word processors).
-
Your application exits spontaneously every time you try to open a specific file or group of files.
-
Your application, previously open and working fine, displays odd behavior each time you open a particular file.
-
You have problems saving other files from an application that are open at the same time as a corrupted file.
-
Closing a suspect file seems to improve the performance of the application.

You may experience such problems as an isolated incident (one important file won’t open), or as a cluster, where all files of a particular type appear to be damaged. You might also see that only files created on or near a specific date are affected.
Regardless of the situation, you’re in a mess. You feel you must either accept the loss of the file as gone forever or you’re stuck redoing hours’, days’, or even weeks’ worth of effort. Or you could sit and bemoan the fact that you never did that backup of your files you kept procrastinating.
None of those options sounds ideal, do they?
But you can sometimes turn a no-win scenario around by knowing some of the tricks of the trade in file recovery.
In previous chapters, you and I have discussed
Your PC, its hardware, and its relationship with the Windows operating system and its installed applications
How to protect your system and your data
How to stabilize and resolve various problems you’re likely to experience—either as part of a disaster or as a situation that quickly degrades into one
Let’s tackle the vexing problem of file and application recovery since this is one of the most common, time-consuming, and aggravating issues you may face as a computer user.

When information professionals (the folks charged with protecting major companies’ data) develop plans for dealing with catastrophes, they usually classify potential disasters into several categories. These include:
Hardware Failure Hardware failures occur when a critical piece of hardware, through some flaw or because of serious wear, ceases to do its job.
Human Error Human errors occur when a user unintentionally causes the damage or creates conditions that cause it.
Natural Natural disasters include hurricanes, storms, floods, and earthquakes.
Man-Made Man-made disasters can be any situation that doesn’t fall into the other categories. These can include a worker or family member simply taking out his or her frustrations on a PC or network in a way that may render the system inoperable.
Political/Situational These types of disasters are usually defined as acts of terrorism or sabotage or as the result of riot-induced vandalism.
Thankfully, most of us are far more apt to see natural, human error, and hardware failure disasters than the other types.
But before you start to relax, understand that even the most common disasters can have expensive and incapacitating effects. You’ll read more about this in the next section.
Profile of a Disaster Risk: The Intrepid Upgrader
My friend Kevin is the epitome of someone with more enthusiasm about what his PC can do than willingness to learn how to handle things well and keep them running that way. Although he needs his computer for the business he’s setting up, he tends to take a number of unnecessary risks that frequently leave him either unable to use some part of his system (usually the modem) or stuck with a system that won’t always boot up.
While Kevin keeps his physical system immaculate (you’ll never find dust, for example), his tendency to download and install everything he sees often confuses his Windows configuration and leads to problems running applications. Add to this the fact that whenever Kevin hits a snag, he reinstalls his operating system (losing the updated drivers for his hardware), and you can understand why my head starts to pound whenever he calls to say, “I’ve got this little problem.”
He likes to buy seriously older PC hardware on sale, and this leads to issues of compatibility, especially since he’s not familiar with hardware concepts such as jumpers and COM ports and drivers.
“Why can’t they make this stuff easier to understand?” he frequently bemoans in my ear after he drives his PC a considerable distance to have me get it operational again.
The last two times this happened, I made him promise to run a full backup or create a drive image (an actual image of the contents and structure of a hard drive) as soon as he returned home. Each time, he told me later, “I would have done it, but it seemed too complicated. But I’ve got this new little problem I was thinking you could help me with…”
Profile of a Disaster Risk: Lightning
It may be hard for you to picture the type of conflagrations often talked about in disaster recovery scenarios. After all, it’s hard to imagine your home or business obliterated in the immediate aftermath of a nuclear attack, bombing, or jumbo jet impact.
So let’s look instead at something that may occur hundreds of times a day around the planet and that can be responsible for a fair amount of damage even though it is so commonplace: a thunderstorm.
As your grandmother always told you, it isn’t the thunder that poses a problem but the electrical atmospheric changes and discharges that occur with lightning. Traditionally, the most violent storms occur when much cooler air moves into a region that has been oppressively hot. A turbulent clash develops, the energy of which must be dissipated somehow, and lightning is the result.
Have you ever seen ball lightning? While this is a rare occurrence, anyone who ever observes this arcing, fiery plasma ball of light and power begins to respect the kind of force that any type of lightning can carry.
Ordinary lightning can hurt your home, office, and electronics both directly and indirectly. Even with some of the limited grounding built into both newer and older homes, energy from lightning can travel inside your home or office, travel along your wiring, and damage the equipment directly, sometimes resulting in fire.
For those who remember or still use an outdoor antenna, you know that lightning can hit the antenna and travel in along the wiring into the back of the TV or radio and blow it out. Likewise, lightning hitting the phone line can send the charge shooting along the phone line into your home or office. In rare instances, it can kill a person talking on the phone when it does. If that phone line is connected to a modem that is in turn connected to your PC (the typical setup for a regular dialup Internet connection), the charge can enter the PC, frying the modem and sometimes frying the motherboard the modem is connected to. Since everything else in a PC is connected either directly or indirectly to the motherboard, the result can be a smoking heap.
Even if the lightning strike doesn’t occur immediately near your home or office, you’re still at risk because you’re connected to a string of other potential strike sites. For example, if your power substation takes a powerful strike from lightning, it can cause surges or at least create electrical ripples throughout the neighborhood the substation serves. The same is true when a car accidentally plows into a utility pole carrying above-ground power lines.
Other Potential Disasters
Also bear in mind that violent storms can bring about flash flooding, which may endanger basement and ground level areas where electronics may be located. Heavy rains can also send rain cascading into open windows and through poor roofing.
Not a lot of PCs—or TVs, stereos, kitchen appliances, and so on—survive being immersed, even when they are turned off and disconnected from power at the time the water reaches them. If they are plugged in and in use at the time the water hits, they short out and may likely become a total loss. Unfortunately, that’s the good news, because as long as the power connection is in place, the electronics pose a serious danger for electrical shock if you touch them or touch anything that touches them (for example, the corner of a metal desk on which a wet PC sits).
Types of Disasters
Believe it or not, much damage can also occur well after a storm is finished. Many people, especially since the Year 2000 scare when everyone was afraid the power grids might shut down, have installed backup generators for their homes and offices to keep at least minimal services available when the main power supply is out. But an improperly installed generator can send a powerful surge out along the power lines once power is restored, sometimes resulting in a second blackout or at least spotty power all along the line. Likewise, damaged electronics and appliances that weren’t fully killed before the power winked out may roar to life again once the power is restored, causing further problems or fire risk.
Where I live in a very rural area of northern New England, we often see “rocking” power, where a storm hits along the electrical chain and sends the power switching on and off several times a minute. Over time, even with protective measures employed, I’ve still lost some equipment to this kind of electrical misbehavior.
The message I’m trying to convey is don’t be scared of the potential damage but understand that it doesn’t take a terrorist attack or other horrific event to put you at risk. Mother Nature supplies more than enough phenomena to make emergency planning a necessity for everyone.
Software, Solution for Crashed Hard Disk
Posted by ALMeD Labels: Data Recovery, Download, Free Data Recovery ToolsYour computer or laptop hard disk crashed, do not worry. Don't panic. Everything has a solution. Data recovery is very expensive. Hard disk will be disastrous for many reasons. Here you'll find a few possibilities and solutions.
1) Data Disc Recovery (Tool)
Data Disk Recovery is a free hard drive recovery tool. DDR can effective scan and recover data. FAT and NTFS format hard disks, efficient. Features;
- Powerful searchind hard drive,
- SHİFT+DELETE, recover data lost on FAT
- Data recovery each part from the drive
DOWNLOAD
2) PC Inspector File Recovery
Data recovery is risky but good data recovery tools, there is less risk. The best way for data recovery industry :D. PC Inspector File Recovery very good data recovery software. Come on, let's look at the features of this tool.
- FAT and boot sector working
- User-friendly and GUI.
- Excellent integration with Windows
- Recovers files with the original date and timestamp.
- Recover files even when the header entry is no longer available.
- Supports many formats. (Archiving programs)
DOWNLOAD
3 Freeware Data Recovery Tools - Easy Way
Posted by ALMeD Labels: Data Recovery, Download, Free Data Recovery ToolsNow you will see 3 good data recovery tool. These tools are useful but Do not use these tools is important files. Let's start.
1) PhotoRec (Windows/Mac/Linux)
PhotoRec data recovery software, video, images, documents, hard disk, including CDRom was designed to recover files. PhotoRec is free, this open source multi-platform application is distributed under GNU Public License.
PhotoRec runs under
* DOS/Win9x
* Windows NT 4/2000/XP/2003/Vista
* Linux
* FreeBSD, NetBSD, OpenBSD
* Sun Solaris
* Mac OS X
and can be compiled on almost every Unix system.
2) TestDisk (Windows/Mac/Linux)
TestDisk is amazing open source software for your PC.
TestDisk can
* Fix partition table, recover deleted partition
* Recover FAT32 boot sector from its backup
* Rebuild FAT12/FAT16/FAT32 boot sector
* Fix FAT tables
* Rebuild NTFS boot sector
* Recover NTFS boot sector from its backup
* Fix MFT using MFT mirror
* Locate ext2/ext3 Backup SuperBlock
* Undelete files from FAT, NTFS and ext2 filesystem
* Copy files from deleted FAT, NTFS and ext2/ext3 partitions.
3) Recuva (Windows)
Recuva most recognized. Windows users know. :D Runs under Microsoft Windows Vista, XP, 2003, 2000 and 98. The tool can also be used to recover files deleted from flash/USB drives, memory cards or MP3 players.

In the computer age, users, organizations, businesses to store data in computer systems. This storage of data;
- Magnetic: Hard Disk, floppy disk, tape backup cartridges
- Optical: CD and DVD, BluRay
- Electronic : Flash disk, memory card
Stored in the data base of physical or logical, be unattainable is "Data Loss". Causes and types of data loss;
1) Data storage media provide access to data logical regulations (file system) deleting or damage.
2) Deleting files or formatting.
3) Database files, documents have internal deterioration.
4) Data storage media is corrupted or damaged by the physical.
Data Recovery
Can not be reached, corrupt, deleted, lost data, data recovery is to restore private methods. Data recovery professional knowledge, experience requires. For physical damage, spare parts, special equipment is needed. Logical in structure damage, detailed sector-based and long work requires. Most important issues and should be considered, protection of the existing situation. Most small an error solution makes it difficult.
a) File System Recovery of Damage
Computer systems used in data storage media data and program files be saved on a regular basis and to follow. For this, file systems have been developed. FAT, NTFS, NWFAT, Ext2FS, CDFS. In the structure of data storage media system, there are system field ve data field.
System Field; description files, address files.
Data Fİeld ; files and defining sub-groups
System is very important. Advanced disk analysis and data recovery tools with
system is repaired.
b) Formatting and Delete Recovery
Files are deleted two basic information remains. First, name of the file, properties, and initial location. Second, knowledge of cluster chain created. Magnetic data storage media often random login is used. Automatic data recovery programs often under 30% and have success.

Data loss is one of the files are deleted. İntentionally or accidentally deleted files can. After deleting data. "Oooo shit!" we say. But this is not the solution. Many users delete the file uses the DELETE key. In fact, DELETE is the key to delete data securely. Some users are using the SHİFT + DELETE button. Files will not go into recycling. In fact, DELETE or SHİFT + DELETE to delete a file even if the data will remain on the disc surface.
Delete files on the disk surface data will stay.
Intervention Method
Do not ever do a transaction. Do not save files, Do not install programs, no play game. Data recovery software download now. To scan your disk. If data is very important without any intervention, GO! Data recovery company...
Suggestions Software
Recuva. It is free and quality software. User friendly. Each may need an DOWNLOAD NOW

Since when do you use a computer? 1 day? 10 years? No matter what happens to have a good backup system is needed. Memories and film archives that are important. For many years, archives have accumulated. Is not in a moment. To lose all the data? Nobody does not like. Then you need a good backup system.
How are backups being done?
The important thing is the computer's hard disk file in another location in the extra copy. The easiest way to make a backup of data as a whole is in an external hard disk. You can also upload them to online file hosting services or having your multiple drives at RAID 1 configuration.
1) Online file hosting
There are many sites to host the files online. But very few sites are reliable. These sites provide free or premium service. I'm sure you've heard about RapidShahre, SaveFile or BoxNet. Rapidshare the best of me. If you are premium members never delete files. Forever. You can host your files forever. Without danger of deletion. (but this mad world, everything can be)
Security
If you need security for your files, you can password protect your files using Winrar. A simple .zip or .rar file with a strong encryption (password) is almost impossible to be opened without the correct password. Do not forget! sure each computer is formatted. Be dignified.
2) External Hard Drives
The easiest method to do backup is by having external hard drive. External hard drives for extra storage or backup is used. I have a few suggestions to you. Speed and capacity price increases. Make up your mind.
a) CMS Products V2 Desktop Backup System 1tb
Drive size (GB): 1000GB, Supported Interface(s): External SATA-300, USB 2.0, Speed (RPM): 7200, Buffer Size (MB): 16, Cost per Gigabyte: $0.18,
Bottom Line: This top-flight performer provides a software/hardware combination for creating a bootable backup drive.
170-190$
b) Western Digital My Book World Edition 1TB
Drive size (GB): 1000GB, Supported Interface(s): External SATA-300, USB 2.0, FireWire 400, Speed (RPM): 7200, Buffer Size (MB): 16, Cost per Gigabyte: $0.21,
Bottom Line: Reasonably priced for a single 1TB drive, this model lacks the performance oomph of some of its competitors.
200-210$
c) WiebeTech ToughTech FS 500GB
Drive size (GB): 500GB, Supported Interface(s): External SATA-300, USB 2.0, FireWire 400, Speed (RPM): 7200, Buffer Size (MB): 16, Cost per Gigabyte: $0.41,
Bottom Line: Fast drive comes in a sleek, accessible (via tools) chassis, but lacks bundled software.
How to Speed Up Windows XP in Seconds ? Easy Way
Posted by ALMeD Labels: Data Recovery, Download, Free Data Recovery Tools
Windows of the complaint will be slow. I broke the keyboard and mouse. But this is not the solution. There are many techniques to speed up the computer. And easy. Keep reading to learn.
Blue screens, system errors, high in most cases it probably has to do with the Windows registry system. When you download and install so many applications onto your windows in happens that some applications, games, programs aren't installed/uninstalled properly.
It is important to understand the Windows registry. For each hardware and software to run Windows uses the Windows registry. This system is very sensitive. We want to accelerate Windows XP. That time. I need to repair the corrupted registry. We will minimize errors in Windows. That time computer is not slow. To repair the registry requires a very technical information. You can not do ourselves. The best way to accelerate Windows XP. It is a good software. This software should repair the registry. You should fix the error encountered. Then the computer programs that load quickly.
Quickly scan, repair and speed up Windows XP in seconds right now!
We are living in the age of technology. Therefore, important information, memories and photos, projects are saved on the hard disk. If damage to the hard disk all within one second is lost. Computer users usually don’t back up their files because of a absolute menace still exists.
A simple method that we people on customer when backing up their computers is to arrange all file on the computer that needs to be back up.
Generally, these files are locus on the “My Documents” and desktop. I create a several files on the desktop, limit of each folder to the size of a disk whether it be a CD or DVD depending on how I am backing up my files. This way, every file on the desktop equivalent to one back up disk.
I transfer entire the files from “My Documents” and put them in the folders that I created. Later the files are in the relative folders on the desktop.
Click on the “Write Files to Disk” and follow the on screen wizard.
Once you are finished backing up all your files, move them back to “My Computer” or remove them if you need the space.
Your computer files regularly to avoid losing it. Regular basis and do not lose data.
Hello, this site you will write data recovery articles. What is data recovery? Data recovery is the process of salvaging data from damaged, failed, corrupted, or inaccessible secondary storage media when it cannot be accessed normally. Computer data is generated from 1 and 0. You’ll remember the Matrix film there “1234567890*-é!’^+%&/()=?_” seen different characters. İn the market 4.200Rpm, 5400 Rpm, 7200 Rpm, 10.000Rpm speed discs are sold in.
Data recovery example;
A txt file. This txt file while recording, eg is “101101″.
Must be written to the disc surface: 101101.
Error occurs and, is “110010″. That is a data loss situation. At this point enters the data recovery circuit. There are different ways to recover data. Here it will handle data recovery issues.



